Apple
Mercenary spyware is one of the most difficult threats to combat. It targets an infinitesimal percentage of the world, making it statistically unlikely that most of us will ever see it. And yet, because the sophisticated malware selects only the most influential individuals (think diplomats, political dissidents, and lawyers), it has a devastating effect far out of proportion to the small number of people infected.
This puts device and software makers in a difficult position. How do you build something to protect what’s probably well below 1 percent of your user base from malware built by companies like NSO Group, creator of clickless exploits that instantly turn fully updated iOS and Android devices into advanced eavesdropping devices.
No safety hose oil here
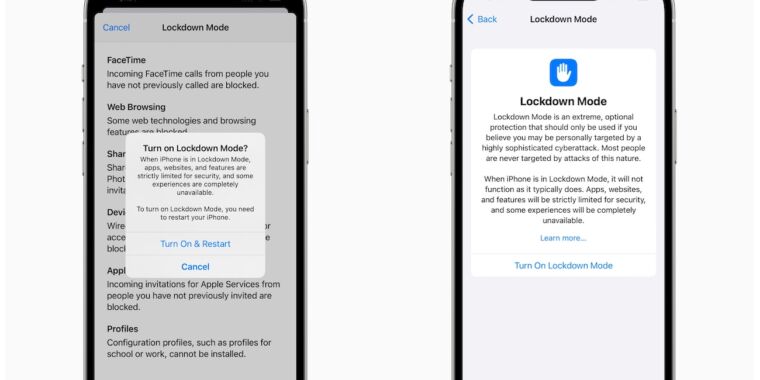
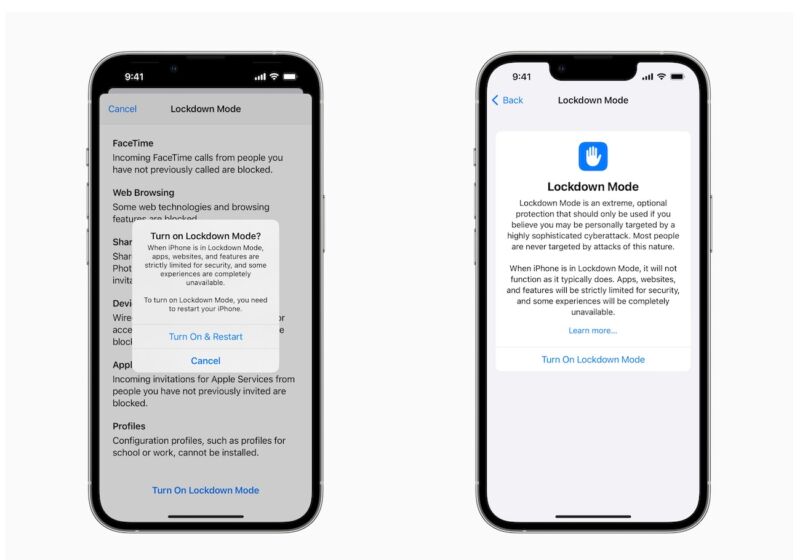
On Wednesday, Apple previewed an ingenious feature it plans to add to its flagship operating systems in the coming months to counter the threat of rental spy spyware. The company is candid – almost to your face – that Lockdown Mode is an option that will degrade the user experience and is intended for only a small number of users.
“Lockdown Mode provides an extreme, optional level of security for the few users who, because of who they are or what they do, could be personally targeted by some of the most advanced digital threats, such as those from NSO Group and other private companies identified by the state sponsored spyware for mercenaries,” the company said. “Enabling Lockdown Mode in iOS 16, iPadOS 16, and macOS Ventura further strengthens device defenses and strictly limits certain functionality, significantly reducing the attack surface that could potentially be exploited by highly targeted rental spy spyware.”
As Apple says, Lockdown mode disables all kinds of protocols and services that work normally. Just-in-time JavaScript, an innovation that speeds up performance by compiling code on the device at runtime, doesn’t run at all. That is probably a defense against using JiT spraying, a common technique used in malware exploitation. Lockdown mode also prevents devices from enrolling in what is known as mobile device management used to install special organization-specific software.
The full list of restrictions is:
- Messages: Most types of message attachments, except images, are blocked. Some features, such as link previews, are disabled.
- Web browsing: Certain complex web technologies, such as just-in-time (JIT) JavaScript compilation, are disabled unless the user excludes a trusted site from Lockdown mode.
- Apple services: Incoming invitations and service requests, including FaceTime calls, will be blocked if the user has not previously sent the initiator a call or request.
- Wired connections to a computer or accessory are blocked when iPhone is locked.
- Configuration profiles cannot be installed and the device cannot be enrolled in mobile device management (MDM) while the lock mode is enabled.
It’s helpful that Apple is candid about the extra friction that Lockdown adds to the user experience, because it underscores what every security professional or hobbyist knows: Security always results in a tradeoff with usability. It’s also encouraging to hear that Apple plans to allow users to list the sites that are allowed to offer JIT JavaScript in Lockdown mode. Fingers crossed that Apple allows a similar admission list of trusted contacts.
Lockdown mode is important for many reasons, not least because it comes from Apple, a company hypersensitive to customer perception. Officially recognizing that its customers are vulnerable to the scourge of rental spyware is a big step.
But the move is great because of its simplicity and concreteness. No safety hose oil here. If you want better security, learn to do without the services that pose the greatest threat. John Scott-Railton, a Citizen Lab researcher who knows a thing or two about counseling victims of NSO spyware, said Lockdown Mode provides one of the first effective courses that vulnerable individuals can take without turning off their devices altogether.
“If you let users know that they are being targeted by advanced threats, they will inevitably ask, ‘How can I make my phone more secure?’ He wrote.’ “We haven’t had many good, honest answers that really impress. Hardening a consumer device is really unattainable.”
3/There is a common mental barrier among major platforms and OS developers around mainstreaming high-security features.
Many unavoidable considerations, such as:
– Worse user experience (especially vs. the competition!)
– Breaking Features
– Need more customer support resources, etc.— John Scott-Railton (@jsrailton) July 6, 2022
Now that Apple has opened the door, it’s inevitable that Google will follow suit with its Android OS, and it shouldn’t be surprising that other companies follow suit as well. It could also be the start of a useful discussion in the industry about broadening the approach. If Apple allows users to disable unsolicited messages from unknown people, why can’t it provide an option to disable the built-in microphone, camera, GPS, or cellular capabilities?
One thing everyone should know about Lockdown Mode, at least as described on Wednesday by Apple, is that it doesn’t stop your device from connecting to mobile networks and broadcasting unique identifiers like IMEI and ICCID. That is not a criticism, but a natural limitation. And compromises are an essential part of security.
So if you are like most people you will never need Lockdown Mode. But it’s great that Apple is offering it, because it will make us all safer.