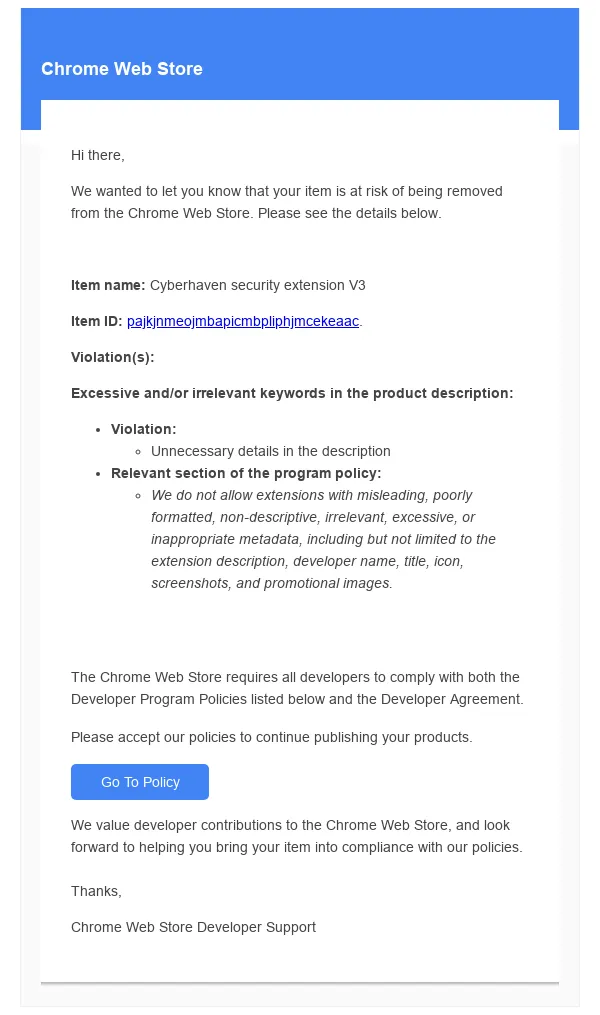
Screenshot of the phishing email sent to Cyberhaven extension developers.
Credit: Amit Assaraf
A link in the email led to a Google consent screen requesting access rights to an OAuth application called Privacy Policy Extension. A Cyberhaven developer granted the permission, unknowingly giving the attacker the ability to upload new versions of Cyberhaven's Chrome extension to the Chrome Web Store. The attacker then used the permission to remove the malicious version 24.10.4.
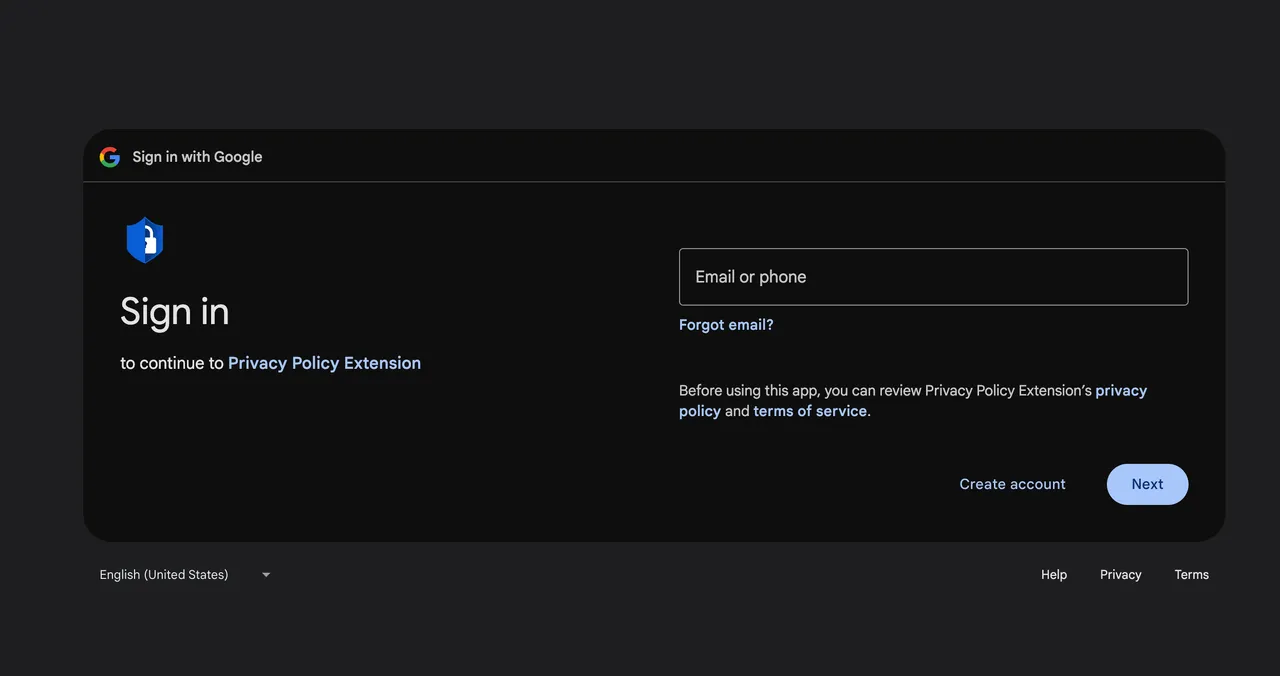
Screenshot of Google's permission request.
Credit: Amit Assaraf
As news of the attack spread in the early hours of December 25, developers and researchers discovered that other extensions were being targeted, in many cases successfully, by the same spearphishing campaign. John Tuckner, founder of Secure Annex, a browser extension analytics and management company, said he was aware of 19 other Chrome extensions that had been similarly affected as of Thursday afternoon. In all cases, the attacker used spearphishing to push a new malicious version, and custom look-alike domains to issue payloads and receive authentication data. Collectively, the twenty extensions had 1.46 million downloads.
“For many I speak to, managing browser extensions may be a lower priority item in their security program,” Tuckner wrote in an email. “People know they can pose a threat, but rarely do teams take action against them. We've seen it many times in security [that] One or two incidents can cause a reevaluation of an organization's security posture. Incidents like these often leave teams looking for a way to gain visibility and understanding of the impact on their organizations.”
The first compromise took place in May 2024. Tuckner provided the following spreadsheet:
| Name | Identity card | Version | Patch | Available | Users | Start | End |
| VPNCity | nnpnnpemnckcfdebeekibpiijlicmpom | 2.0.1 | FALSE | 10,000 | 12/12/24 | 31-12-24 | |
| Parrot talks | kkodiihpgodmdankclfibbiphjkfdenh | 1.16.2 | WHERE | 40,000 | 25/12/24 | 31-12-24 | |
| Ustem | oaikpkmjciadfpddlpjjdapglcihgdle | 1.0.12 | WHERE | 40,000 | 26-12-24 | 31-12-24 | |
| Internal VPN | dpggmcodlahmljkhlmpgpdcffdaoccni | 1.1.1 | 1.2.0 | WHERE | 10,000 | 25/12/24 | 29/12/24 |
| Bookmark Favicon Changer | acmfnomgphggonodopogfbmkneepfgnh | 4:00 am | WHERE | 40,000 | 25/12/24 | 31-12-24 | |
| Castorus | mnhffkhmpnefgklngfmlndmkimimbphc | 4.40 | 4.41 | WHERE | 50,000 | 26-12-24 | 27-12-24 |
| Wayin AI | cedgndijpacnfbdggppddacngjfdkaca | 0.0.11 | WHERE | 40,000 | 19/12/24 | 31-12-24 | |
| Search for Copilot AI Assistant for Chrome | bbdnohkpnbkdkmnkddobeafboooinpla | 1.0.1 | WHERE | 20,000 | 7/17/24 | 31-12-24 | |
| VidHelper – Video downloader | for examplemennebgadmncfjafcemlecimkepcle | 2.2.7 | WHERE | 20,000 | 26-12-24 | 31-12-24 | |
| AI Assistant – ChatGPT and Gemini for Chrome | bibjgkidgpfbblifamdlkdlhgihmfohh | 0.1.3 | FALSE | 4,000 | 31/05/24 | 25/10/24 | |
| TinaMind – The GPT-4o powered AI assistant! | befflofjcniongenjmbkgkoljhgliihe | 2.13.0 | 2.14.0 | WHERE | 40,000 | 15/12/24 | 20/12/24 |
| Bard AI chat | pkgciiiancapdlpcbppfkmeaieppikkk | 1.3.7 | FALSE | 100,000 | 5-09-24 | 22/10/24 | |
| Reader mode | llimhhconnjiflfimocjggfjdlmlhblm | 1.5.7 | FALSE | 300,000 | 18/12/24 | 19/12/24 | |
| Primus (formerly PADO) | oeiomhmbaapihbilkfkhmlajkeegnjhe | 3.18.0 | 3.20.0 | WHERE | 40,000 | 18/12/24 | 25/12/24 |
| Cyberhaven Security Extension V3 | pajkjnmeojmbapicmbpliphjmcekeaac | 24.10.4 | 24.10.5 | WHERE | 400,000 | 24/12/24 | 26-12-24 |
| GraphQL Network Inspector | ndlbedplllcgconngcnfmkadhokfaaln | 2.22.6 | 2.22.7 | WHERE | 80,000 | 29/12/24 | 12/30/24 |
| GPT 4 Summary with OpenAI | epdjhgbipjpbbhoccdeipghoihibnfja | 1.4 | FALSE | 10,000 | 31/05/24 | 29-09-24 | |
| Vidnoz Flex – Video Recorder and Video Sharing | cplhlgabfijoiabgkachtigafklbhhdkahj | 1.0.161 | FALSE | 6,000 | 25/12/24 | 29/12/24 | |
| YesCaptcha assistant | jiofmdifioeejeilfkpegipdjiopiekl | 1.1.61 | WHERE | 200,000 | 29/12/24 | 31-12-24 | |
| Proxy switchOmega (V3) | hihblcmlaaademjlakdpicchbjnnnkbo | 3.0.2 | WHERE | 10,000 | 12/30/24 | 31-12-24 |
But wait, there's more
One of the compromised extensions is called Reader Mode. Further analysis revealed that the breach occurred not only in the campaign targeting the other 19 extensions, but also in a separate campaign that launched no later than April 2023. Tuckner said the source of the breach appears to be a code library that developers can use to monetize their extensions. . The code library collects details about every web visit a browser makes. In exchange for including the library in the extensions, developers receive a commission from the library creator.

