While stalking his target, GruesomeLarch carried out attacks that compromised the passwords of several accounts on a web services platform used by the organization's employees. However, two-factor authentication enforced on the platform prevented the attackers from compromising the accounts.
So GruesomeLarch found devices in physically adjacent locations, compromised them, and used them to probe the target's Wi-Fi network. It turned out that the credentials for the compromised web services accounts also worked for accounts on the Wi-Fi network, only 2FA was not required.
To take things further, the attackers hacked into one of the adjacent Wi-Fi devices by exploiting what was a zero-day vulnerability in the Microsoft Windows Print Spooler in early 2022.
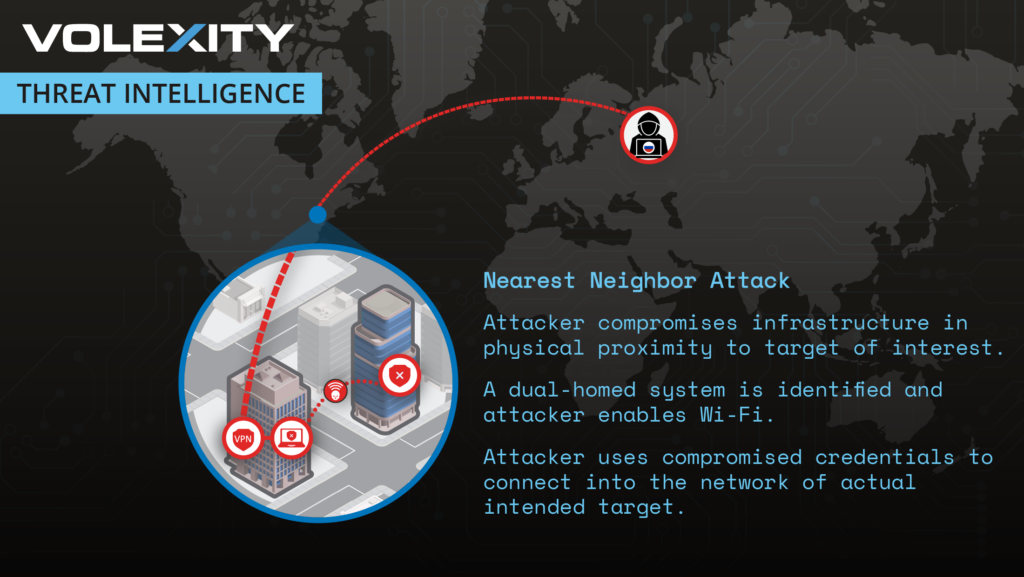
The 2022 hack shows how a single incorrect assumption can undo an otherwise effective defense. For whatever reason (probably an assumption that 2FA on the Wi-Fi network wasn't necessary because attacks had to be close) the target deployed 2FA on the Internet-connecting web services platform (Adair doesn't say which type), but not on the Wi-Fi Fi network. Fi network. That one mistake ultimately torpedoed a robust security practice.
Advanced persistent threat groups like GruesomeLarch – part of the much larger GRU APT with names like Fancy Bear, APT28, Forrest Blizzard, and Sofacy – excel at finding and exploiting these types of flaws.
Volixity's post describing the 2022 attack provides many technical details about the compromise over the many links in this advanced daisy chain attack. There's also useful advice for protecting networks against these types of compromises.

