
According to researchers, hackers spread malware to Windows and Mac users by hacking their internet service providers and then tampering with software updates sent over insecure connections.
The attack, according to researchers at security firm Volexity, worked by hacking into routers or similar types of device infrastructure belonging to an unnamed ISP. The attackers then used their control over the devices to poison domain name system responses for legitimate hostnames delivering updates for at least six different apps written for Windows or macOS. The affected apps included 5KPlayer, Quick Heal, Rainmeter, Partition Wizard, and those from Corel and Sogou.
These are not the update servers you are looking for
Because the update mechanisms did not use TLS or cryptographic signatures to verify connections or downloaded software, threat actors were able to leverage their control over ISP infrastructure to successfully launch machine-in-the-middle (MitM) attacks that redirected targeted users to hostile servers instead of the servers controlled by the affected software makers. These redirects worked even when users used unencrypted public DNS services such as Google's 8.8.8.8 or Cloudflare's 1.1.1.1 instead of the authoritative DNS server provided by the ISP.
“Here's the fun/scary part: This wasn't a hack of the ISPs' DNS servers,” wrote Steven Adair, CEO of Volexity, in an online interview. “This was a compromise of the network infrastructure for Internet traffic. For example, the DNS queries were going to Google's DNS servers, destined for 8.8.8.8. The traffic was intercepted to respond to the DNS queries with the IP address of the attacker's servers.”
In other words, the DNS responses returned by a DNS server are modified once they reach the compromised ISP's infrastructure. The only way an end user could have thwarted the attack would have been to use DNS over HTTPS or DNS over TLS to ensure that lookup results were not tampered with, or to avoid all use of apps that deliver unsigned updates over unencrypted connections.
Volexity created the following diagram illustrating the progression of the attack:
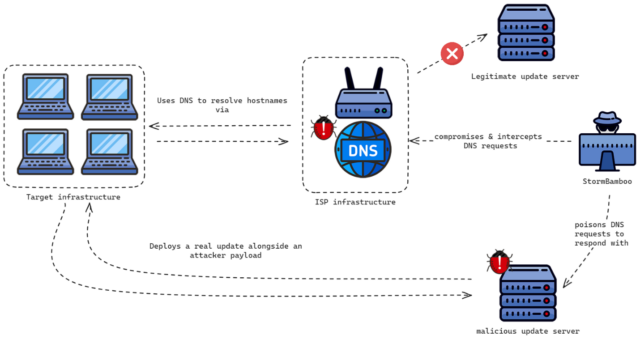
Volexity
For example, the 5KPlayer app uses an insecure HTTP connection instead of an encrypted HTTPS connection to check for an available update and, if so, download a configuration file named Youtube.config. StormBamboo, the industry name used to track the hacking group responsible, used DNS poisoning to deliver a malicious version of the Youtube.config file from a malicious server. This file in turn downloaded a next-stage payload disguised as a PNG image. In fact, it was an executable that installed malware tracked under the names MACMA for macOS devices or POCOSTICK for Windows devices.
MACMA first came to light in a 2021 report published by Google’s Threat Analysis Group, a team that tracks nation-state-backed malware and cyberattacks. The backdoor was written for macOS and iOS devices and offered a full suite of capabilities, including device fingerprinting, screen recording, file downloading and uploading, terminal command execution, audio recording, and keylogging.
POCOSTICK has been in use since 2014. Last year, security firm ESET reported that the malware, which it tracked under the name MGBot, was used exclusively by a Chinese-language threat group known as Evasive Panda.
ESET researchers determined that the malware was being installed via legitimate updates to benign software, but they weren’t sure how. One possibility, the researchers said at the time, was via a supply chain attack that replaced legitimate updates with malicious ones at the source. The other possible scenario was via a MitM attack on the servers delivering the updates. Volexity’s findings now confirm that the latter explanation is the correct one.
In at least one instance in the most recent attacks, StormBamboo forced a macOS device to install a browser plugin that Volexity goes by the name RELOADEXT. The extension masquerades as a web page loader extension to be compatible with Internet Explorer. In fact, Volexity said, it copies browser cookies and sends them to a Google Drive account controlled by the attackers. The data was base64-encoded and encrypted using the Advanced Encryption Standard. Despite the hackers’ care, they still managed to expose the client_id, client_secret, and refresh_token in the malicious extension.
Another technique Volexity observed was StormBamboo’s use of DNS poisoning to hijack www.msftconnecttest.com, a domain Microsoft uses to determine whether Windows devices are actively connected to the internet. By replacing the legitimate DNS resolution with an IP address pointing to a malicious site controlled by the threat actors, they were able to intercept HTTP requests destined for any host.
Adair declined to name the hacked ISP, other than to say it was “not a big one, or one you'd likely recognize.”
“In our case, the incident has been contained, but we see other servers actively serving malicious updates, but we don't know where they are coming from,” he said. “We suspect there are other active attacks globally that we don't have visibility into. This could be due to an ISP compromise or a local compromise of an organization, such as on their firewall.”
As noted, there are many options for preventing these types of attacks, beyond (1) avoiding all software that updates insecurely or (2) using DNS over HTTPS or DNS over TLS. The first method is likely the best, though it will likely mean you’ll have to stop using a preferred app in at least some cases. The alternative DNS configurations are viable, but are currently only offered by a handful of DNS providers, with 8.8.8.8 and 1.1.1.1 being the most well-known.

