Getty Images
Among the files that could potentially go wrong, comes this: An industrial control engineer recently made a workstation part of a botnet after accidentally installing malware that advertised as a means of recovering lost passwords.
Lost passwords are common in many organizations. A programmable logic controller — used to automate processes in factories, power plants, and other industrial environments — could be set up and largely forgotten in the coming years. When a replacement technician later identifies a problem affecting the PLC, they may discover that the now-long-disappeared original engineer never left the passcode before leaving the company.
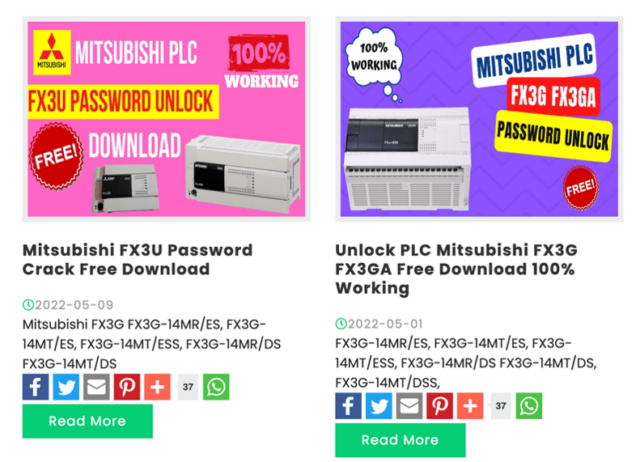
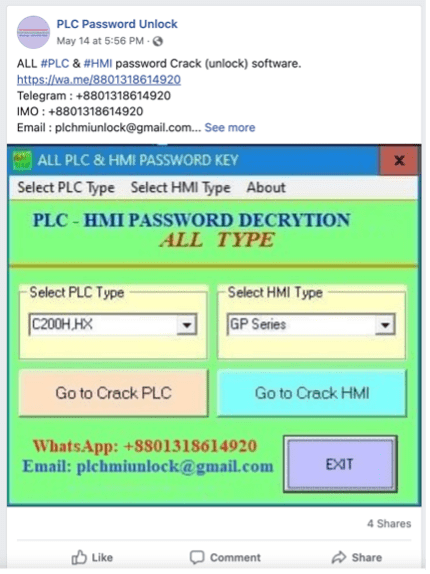
According to a blog post by security firm Dragos, an entire malware ecosystem is trying to take advantage of scenarios like these in industrial facilities. Online ads like the one below promote password crackers for PLCs and human-machine interfaces, the workhorses in these environments.
Dragos
Dragos
When your industrial system is part of a botnet
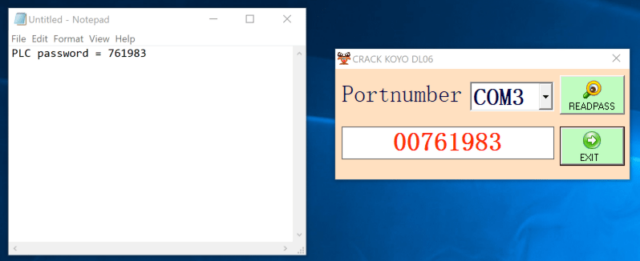
Dragos — which helps companies secure industrial control systems against ransomware, state-sponsored hackers and potential saboteurs — recently conducted a routine vulnerability assessment and discovered that a customer’s system was installed with software that used to provide the human-readable password for the DirectLogic 06, a PLC sold by Automation Direct. The software recovered the password, but not through the normal cryptographic hash cracking method. Instead, the software exploited a zero-day vulnerability in Automatic Direct PLCs that exposed the access code.
Dragos
“Previous research focused on DirectLogic PLCs has resulted in successful cracking techniques,” wrote Dragos researcher Sam Hanson. “However, Dragos found that this exploit does not crack an encrypted version of the password, as historically seen in popular exploitation frameworks. Instead, a specific byte string is sent by the malware dropper to a COM port.”

Dragos
The vulnerability, and a related one also found by Hanson, has now been patched and is tracked as CVE-2022-2033 and CVE-2022-2004. The latter vulnerability can recover passwords and send them to a remote hacker, bringing the severity rate to 7.5 out of a possible 10.
In addition to recovering the password, the software installed on the Dragos customer’s network also installed malware known as Sality. It made the infected system part of a botnet and checked the clipboard of the infected workstation every half second for data related to cryptocurrency wallet addresses.
“If seen, the hijacker replaces the address with one owned by the threat actor,” Hanson said. “This real-time hijacking is an effective way to steal cryptocurrency from users who want to transfer money and increases our confidence that the adversary is financially motivated.”
Hanson went on to say that he found password crackers advertised online for a wide variety of industrial software sold by other companies. They contain:
| Seller and Assets | System type |
| Automation Direct DirectLogic 06 | PLC |
| Omron CP1H | PLC |
| Omron C200HX | PLC |
| Omron C200H | PLC |
| Omron CPM2* | PLC |
| Omron CPM1A | PLC |
| Omron CQM1H | PLC |
| Siemens S7-200 | PLC |
| Siemens S7-200 | Project file (*.mwp) |
| Siemens LOGO! 0AB6 | PLC |
| ABB Codesys | Project file (*.pro) |
| Delta Automation DVP, ES, EX, SS2, EC Series | PLC |
| Fuji Electric POD UG | HMI |
| Fuji Electric Hakko | HMI |
| Mitsubishi Electric FX Series (3U and 3G) | PLC |
| Mitsubishi Electric Q02 Series | PLC |
| Mitsubishi Electric GT 1020 Series | HMI |
| Mitsubishi Electric GOT F930 | HMI |
| Mitsubishi Electric GOT F940 | HMI |
| Mitsubishi Electric GOT 1055 | HMI |
| Pro-Face GP Pro-Face | HMI |
| Pro Face GP | Project file (*.prw) |
| Force VB | PLC |
| Power VH | PLC |
| weintek | HMI |
| Allen Bradley MicroLogix 1000 | PLC |
| Panasonic NAIS F P0 | PLC |
| Fatek FBe and FBs Series | PLC |
| IDEC Corporation HG2S-FF | HMI |
| LG K80S | PLC |
| LG K120S | PLC |
Dragos only tested the malware targeting the DirectLogic devices, but a rudimentary analysis of a few samples revealed that they also contained malware.
“Overall, it seems like there’s an ecosystem for this kind of software,” Hanson said. “Several websites and multiple social media accounts exist, all touting their password ‘crackers’.”
The report is alarming because it illustrates the laxity that still exists in many industrial control environments. The criminals behind the malware that infected the Dragos customer were after money, but there’s no reason why more malicious hackers looking to sabotage a dam, power plant or similar facility couldn’t carry out a similar intrusion with far more serious consequences.

