Researchers have discovered a malicious Android app that can tamper with the wireless router the infected phone is connected to and force the router to send all network devices to malicious sites.
The malicious app, found by Kaspersky, uses a technique known as Domain Name System (DNS) hijacking. Once installed, the app connects to the router and attempts to log into its admin account using standard or common credentials such as admin:admin. If successful, the app turns the DNS server into a malicious server controlled by the attackers. From then on, devices on the network can be redirected to bogus sites that impersonate legitimate sites but spread malware or log user credentials or other sensitive information.
Can spread widely
“We believe that the discovery of this new implementation of the DNS changer is very important in terms of security,” Kaspersky researchers wrote. “The attacker can use it to control all communications from devices using a compromised Wi-Fi router with the rogue DNS settings.”
The researchers continued: “Users connect infected Android devices to free/public Wi-Fi in places such as cafes, bars, libraries, hotels, shopping malls and airports. When connected to a targeted Wi-Fi model with vulnerable settings, the Android malware will compromise the router and affect other devices as well. As a result, it can spread widely in the targeted regions.
DNS is the mechanism that links a domain name such as ArsTechnica.com to 18.188.231.255, the numerical IP address where the site is hosted. DNS lookups are performed by servers operated by a user’s ISP or by services from companies such as Cloudflare or Google. By changing the DNS server address in a router’s management panel from a legitimate address to a malicious one, attackers can cause all devices connected to the router to receive malicious domain queries that lead to similar sites used for cybercrime.
Known as Wroba.o, the Android app has been used for years in several countries, including the US, France, Japan, Germany, Taiwan, and Turkey. Oddly enough, the DNS hijacking technique that the malware is capable of is used almost exclusively in South Korea. From 2019 through most of 2022, attackers lured targets to malicious sites sent via SMS, a technique known as smishing. At the end of last year, the attackers integrated DNS hijacking into their activities in that Asian country.
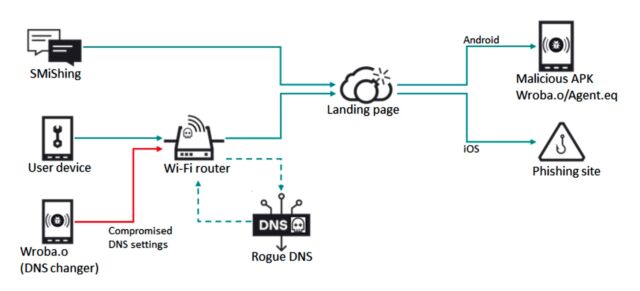
Known in the security industry as Roaming Mantis, the attackers designed the DNS hijack to only work when devices visit the mobile version of a spoofed website, most likely to ensure that the campaign goes unnoticed.
Although the threat is serious, it has one major shortcoming: HTTPS. TLS (Transport Layer Security) certificates that serve as the basis for HTTPS bind a domain name such as ArsTechnica.com to a private encryption key known only to the site operator. People who are directed to a malicious site posing as Ars Technica and using a modern browser receive warnings that the connection is not secure or are asked to approve a self-signed certificate, a practice users should never follow.
Another way to combat the threat is to ensure that the password protecting a router’s admin account is changed from the default password to a strong one.
Still, not everyone is adept at such best practices, leaving them open to visiting a malicious site that looks almost identical to the legitimate site they wanted to access.
“Users with infected Android devices who connect to free or public Wi-Fi networks can spread the malware to other devices on the network if the Wi-Fi network they are connected to is vulnerable,” Thursday’s report said. “Kaspersky experts are concerned about the possibility that the DNS switcher is used to target other regions and cause significant problems.