UPDATE: November 28, 3:20 PM California time. The headline of this message has been changed. This update adds the following further details: This threat is not a UEFI firmware implant or rootkit, it is a UEFI bootkit that attacks the bootloader. The Bootkitty sample analyzed by ESET was not unrecoverable. Below you will find the article where incorrect data has been removed.
Researchers from security firm ESET said on Wednesday that they have found the first UEFI boot kit for Linux. The discovery could mean that UEFI bootkits that have targeted Windows systems in recent years will soon target Linux as well.
Bootkitty – the name unknown threat actors gave to their Linux bootkit – was uploaded to VirusTotal earlier this month. Compared to many Windows UEFI bootkits, Bootkitty is still relatively rudimentary, contains imperfections in key under-the-hood functionality, and lacks the means to infect all Linux distributions except Ubuntu. That has led the company's researchers to suspect that the new boot kit is likely a proof-of-concept release. To date, ESET has found no evidence of actual infections in the wild.
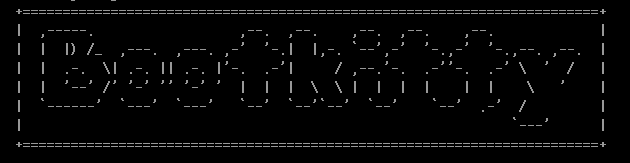
The ASCII logo that Bootkitty can display.
Credit: ESET
Be prepared
Still, Bootkitty suggests that threat actors are actively developing a Linux version of the same kind of bootkit that previously only targeted Windows machines.
“Whether proof of concept or not, Bootkitty marks an interesting step forward in the UEFI threat landscape and shatters the belief that modern UEFI bootkits are Windows-exclusive threats,” ESET researchers wrote. “While the current version of VirusTotal does not pose a real threat to most Linux systems at this time, it highlights the need to be prepared for potential future threats.”
The Bootkitty example found by ESET cannot suppress a defense known as UEFI Secure Boot, which uses cryptographic signatures to ensure that every piece of software loaded during boot is trusted by a computer's manufacturer. Secure Boot is designed to create a chain of trust that prevents attackers from replacing the intended boot firmware with malicious firmware. When Secure Boot is enabled, the device will not boot if a single firmware link in that chain is not recognized.