
Getty Images
Exploit code for a critical vulnerability in printer software became publicly available Monday in a release that could exacerbate the threat of malware attacks that have been going on for five days.
The vulnerability resides in print management software known as PaperCut, which has more than 100 million users from 70,000 organizations, according to the company’s website. When this post went live, the Shodan search engine showed that nearly 1,700 copies of the software had been posted on the Internet.
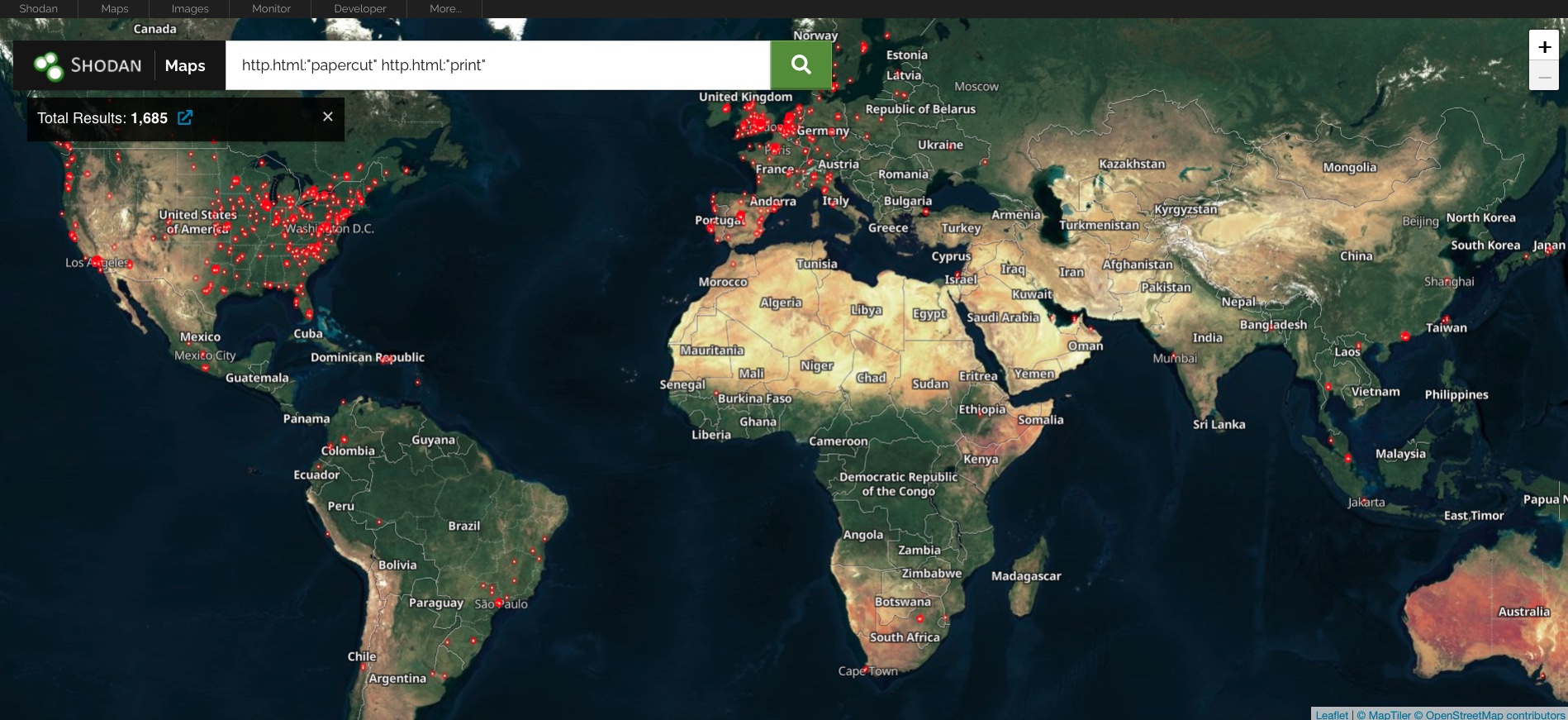
World map with locations of PaperCut installations.
Last Wednesday, PaperCut warned that a critical vulnerability it patched in its software in March was under active attack against machines that had yet to install the March update. The vulnerability, tracked as CVE-2023–27350, has a severity score of 9.8 out of 10. It allows an unauthenticated attacker to remotely execute malicious code without logging in or entering a password. to give. A related vulnerability, tracked as CVE-2023–27351 with a severity rating of 8.2, allows unauthenticated attackers to extract usernames, full names, email addresses, and other potentially sensitive data from unpatched servers.
Two days after PaperCut revealed the attacks, security firm Huntress reported that it found threat actors exploiting CVE-2023-27350 to install two pieces of remote management software — one known as Atera and the other Syncro — on unpatched servers . Evidence then showed that the threat actor used the remote management software to install malware known as Truebot. Truebot is linked to a threat group known as Silence, which has ties to the ransomware group known as Clop. Previously, Clop used Truebot in in-the-wild attacks that exploited a critical vulnerability in software known as GoAnywhere.
“While the ultimate purpose of the current activity using PaperCut’s software is unknown, these links (albeit somewhat indirect) to a known ransomware entity are of concern,” the Huntress researchers wrote in their report Friday. “Possibly, the access gained through PaperCut exploitation can be used as a foothold leading to subsequent movements within the victim network and ultimately to the deployment of ransomware.”
Huntress gave a broad description of the vulnerabilities and how to exploit them. It also published the video below showing an exploit in action. However, the company has not released the exploit code.
PaperCut CVE-2023-27350 proof-of-concept exploitation.
The exploit works by adding malicious entries to one of the template printer scripts that are present by default. Disabling security sandboxing allows the malicious script to access the Java runtime directly and execute code from there on the main server. “As intended, the scripts only contain functions that serve as hooks for future execution, but the global scope is executed immediately after saving, and therefore a simple printer script edit can be used to achieve remote code execution,” explains Huntress.
On Monday, researchers from security firm Horizon3 published their analysis of the vulnerabilities, along with proof-of-concept exploit code for the more serious ones. Similar to the PoC exploit described by Huntress, it uses the authentication bypass vulnerability to manipulate built-in scripting functionality and execute code.
On Friday, Huntress reported that there were about 1,000 Windows machines with PaperCut installed in the customer environments it protects. Of those, about 900 remained unpatched. Of the three macOS machines it monitored, only one was patched. Assuming the numbers are representative of PaperCut’s larger install base, the Huntress data suggests that thousands of servers are still under threat from exploitation. As noted earlier, nearly 1,700 servers are easy to find over the Internet. Additional detective work may be able to find even more.
Any organization using PaperCut should ensure it is running PaperCut MF and NG versions 20.1.7, 21.2.11, and 22.0.9. PaperCut and Huntress also offer workarounds for organizations that can’t update right away. Huntress and Horizon3 also provide indicators that PaperCut users can check to determine if they have been exposed to exploits.

