
Getty Images
Federal prosecutors on Wednesday charged six people with allegedly operating websites that launched millions of powerful distributed denial-of-service attacks against a wide range of victims on behalf of millions of paying customers.
The sites promoted themselves as startup or stressor services designed to test the bandwidth and performance of customers’ networks. Prosecutors said in court documents that the services were used to redirect massive amounts of junk traffic to third-party websites and Internet connections that customers sought to remove or seriously restrict. Victims included educational institutions, government agencies, gaming platforms and millions of individuals. In addition to indicting six defendants, prosecutors also seized 48 internet domains associated with the service.
“These booter services allow anyone to launch cyberattacks that harm individual victims and compromise everyone’s access to the Internet,” Martin Estrada, the U.S. Attorney for the Southern District of California, said in a statement. “This week’s sweeping law enforcement activity is an important step in our ongoing efforts to root out criminal behavior that threatens Internet infrastructure and our ability to function in a digital world.”
The services offered user interfaces that were essentially the same except for cosmetic differences. The screenshot below shows the web panel offered by orphicsecurityteam.com starting February 28. It allowed users to enter a target’s IP address, the network port, and the specific type of attack they wanted. The panel allowed users to choose different methods to amplify their attacks. Amplification involved bouncing a relatively small amount of specially crafted data to a remote server in a way that caused the server to bombard the intended victim with payloads as much as 10,000 times larger.
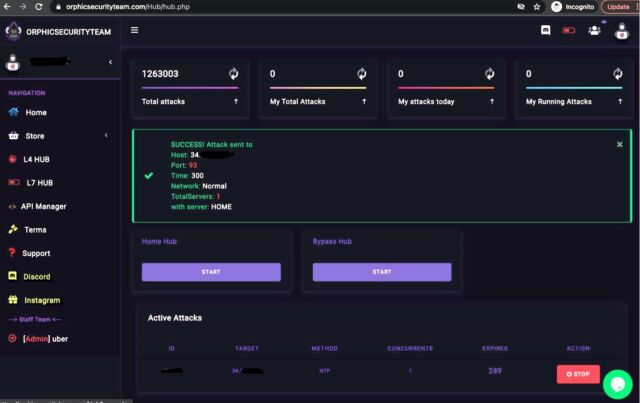
United States Department of Justice
Ironically, most DDoSs relied on DDoS protections, such as those provided by the content delivery network Cloudflare, to avoid being removed in DDoSs themselves. In some cases, defendants relied on Cloudflare’s free tier, while others used a more advanced tier that required payment.
According to an affidavit filed Wednesday, some services had a staggering number of registered customers and attacks were launched. For example, logs indicate that a service called ipstressor.com had 2 million registered users, of which 1 million performed DDoSes. The service has performed or attempted to perform 30 million DDoSes between 2014 and 2022. Securityteam.io allegedly ran or tried
1.3 million attacks and had 50,000 registered users. Prosecutors said astrostress.com carried out or attempted to carry out 700,000 DDoSe’s and had 30,000 registered users.
The seized domains were:
- anonboot.com
- api-sky.xyz
- astro stress. com
- booter.vip
- brrrsecurity.org
- cyberstress.us
- dragonstresser.com
- dreams-stresser.io
- freestresser.zo
- instant-stresser.com
- ipstress.vip
- ipstresser.wtf
- orphicsecurityteam.com
- overstresser.com
- quantum stresser.net
- redstresser.cc
- royal stresser. com
- silentstress.net
- stresser.app
- stresser.dear
- stresser.gg
- stresser.is
- stresser.net/stresser.org
- stresser.so
- stresser.top
- truesecurityservices.io
- vdos-s.co
- zero stresser. com
- ipstresser.xyz
- kraysec.com
- securityteam.io
- ipstresser.us
- stresser.shop
- exotic-booter.com
- mcstorm.io
- nightmarestresser.com
- shock-stresser.com stresserai.com
- sun stresser. com
The six persons charged were:
- Jeremiah Sam Evans Miller, aka “John The Dev,” 23, of San Antonio, Texas, is charged with conspiracy to violate and violate the Computer Fraud and Abuse Act in connection with the alleged operation of a booter service called RoyalStresser .com (formerly known as Supremesecurityteam.com).
- Angel Manuel Colon Jr., aka “Anonghost720” and “Anonghost1337,” 37, of Belleview, Florida, is charged with conspiracy to violate and violate the computer fraud and abuse law related to the alleged operation of a startup service called SecurityTeam.io.
- Shamar Shattock, 19, of Margate, Florida, is facing charges of conspiracy for allegedly running a booter service known as Astrostress.com.
- Cory Anthony Palmer, 22, of Lauderhill, Florida, is facing charges of conspiracy for allegedly running a booter service known as Booter.sx.
- John M. Dobbs, 32 of Honolulu, Hawaii, is charged with complicity in computer fraud and abuse violations related to the alleged operation of a startup service called Ipstressor.com, also known as IPS, between 2009 and November 2022.
- Joshua Laing, 32, of Liverpool, New York, is charged with complicity in computer fraud and abuse violations related to the alleged operation of a startup service called TrueSecurityServices.io between 2014 and November 2022.
All six have yet to enter a plea and are expected to appear in court early next year.
The charges and seizures are part of “Operation PowerOFF”, an ongoing campaign by international law enforcement agencies to dismantle criminal DDoS-for-hire services.

