
Getty Images
Pro-Russian threat actors continue their relentless pursuit of Ukrainian targets, with a series of campaigns including fake Android apps, hacking attacks that exploit critical vulnerabilities, and email phishing attacks that attempt to collect credentials, Google researchers said.
One of the more recent campaigns came from Turla, a Russian-speaking advanced, persistent threat actor who has been in business since 1997 and is one of the most technically advanced in the world. According to Google, the group targeted pro-Ukrainian volunteers with Android apps posing as launch pads for carrying out denial-of-service attacks on Russian websites.
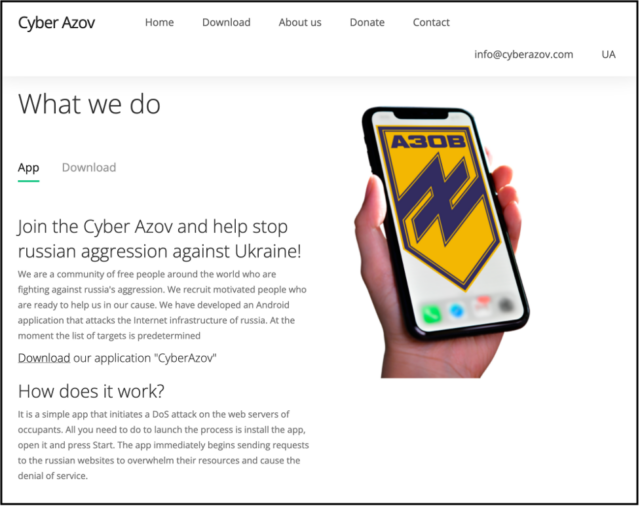
“All you need to do to start the process is install the app, open it and press start,” claimed the fake website promoting the app. “The app immediately starts sending requests to the Russian websites to overwhelm their resources and cause denial of service.”
According to a researcher from Google’s threat analysis group, the app sends a single GET request to a target website. Behind the scenes, another Google researcher told Vice that the app is designed to map the user’s internet infrastructure and “find out where the people are who might be carrying out these types of attacks.”
The apps, hosted on a domain that is trolling Ukraine’s Azov regiment, mimicked another Android app Google first spotted in March that also claimed to carry out DoS attacks on Russian sites. Unlike the Turla apps, stopwar.apk, as the latter app was called, sent a continuous stream of requests until the user stopped them.
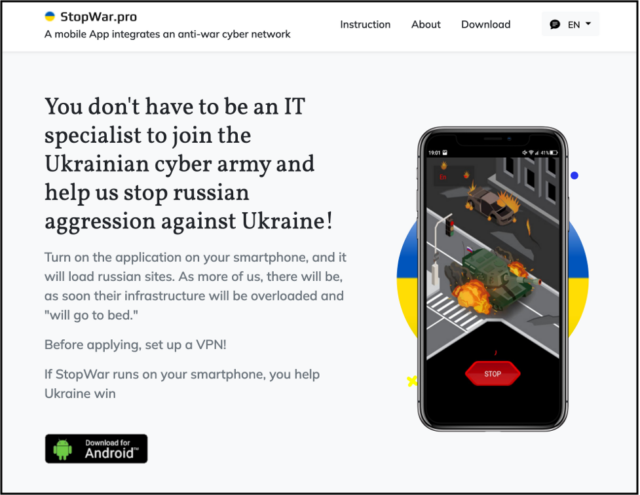
“Based on our analysis, we believe that the StopWar app was developed by pro-Ukrainian developers and was the inspiration for what Turla actors based their fake CyberAzov DoS app on,” wrote Google researcher Billy Leonard.
Other Kremlin-sponsored hacking groups have also targeted Ukrainian groups. Campaigns include the exploitation of Follina, the name given to a critical vulnerability in all supported versions of Windows that has been actively attacked in the wild as a zero-day for over two months.
Google researchers confirmed a June CERT-UA report that said another Kremlin-sponsored hacking group — followed by various names, including Fancy Bear, known as Pawn Storm, Sofacy Group, and APT28 — also exploited Follina in an attempt to infect targets with malware known as CredoMap. In addition, Google said Sandworm — yet another group sponsored by the Russian government — also exploited Follina. That campaign used compromised government accounts to send links to Microsoft Office documents hosted on compromised domains, primarily targeting media organizations in Ukraine.
CERT-UA
Security firm Palo Alto Networks reported Tuesday that Russian hacking group Cloaked Ursa (aka APT29, Nobelium and Cozy Bear) had also ramped up malware attacks, in part by creating malicious files, since the Russian invasion began. available for download on Dropbox and Google Drive. US and British intelligence agencies have publicly attributed APT29 to the Russian Foreign Intelligence Service (SVR).
“This is consistent with the group’s historical focus, which dates back to malware campaigns against Chechnya and other former Soviet bloc countries in 2008,” Palo Alto Networks researchers Mike Harbison and Peter Renals wrote. More recently, APT29 has been linked to a US Democratic National Committee hack discovered in 2016 and attacks on the SolarWindows supply chain as of 2020.
Not all threat groups targeting Ukraine are sponsored by the Kremlin, Google said. Recently, a financially motivated actor was followed when UAC-0098 posed as the State Tax Agency of Ukraine and delivered malicious documents attempting to exploit Follina. Google said the actor is a former initial ransomware access broker who previously partnered with the Conti ransomware group.
On Wednesday, the US Cyber Command shared technical details regarding what the agency says are various types of malware that have targeted Ukrainian entities in recent months. The malware samples are available on VirusTotal, Pastebin, and GitHub. Security firm Mandiant said two separate spy groups used the malware, one tracked as UNC1151 and attributed by Mandiant to the Belarusian government and the other tracked as UNC2589, which the company said is “believed to be acting in support of Russian government interests and has carried out extensive espionage collection in Ukraine.”
The European Union also called on the Russian government this week, noting that a recent distributed denial-of-service campaign was just the latest example of cyberattacks it has launched since the invasion.
“Russia’s unprovoked and unwarranted military aggression against Ukraine has been accompanied by a significant increase in malicious cyber activity, including a striking and worrying number of hackers and hacker groups targeting critical entities worldwide indiscriminately,” EU officials wrote. “This proliferation of malicious cyber activities, in the context of the war against Ukraine, creates unacceptable risks of spillovers, misinterpretations and potential escalation.”

