
Android malware developers are ramping up billing fraud with apps that disable Wi-Fi connections, covertly subscribe users to expensive wireless services and intercept text messages, all in an effort to collect hefty fees from unsuspecting users, Microsoft said Friday.
This threat class has been a reality on the Android platform for years, as evidenced by a family of malware known as Joker that has infected millions of phones since 2016. Despite awareness of the issue, little attention has been paid to the techniques used by such “toll fraud” malware. Enter Microsoft, which has published a technical deep dive on the issue.
The billing mechanism exploited in this type of fraud is WAP, short for Wireless Application Protocol, which provides a means of accessing information over a cellular network. Mobile phone users can subscribe to such services by visiting a service provider’s web page while their devices are connected to a mobile service and then clicking a button. In some cases, the carrier will respond by texting a one-time password (OTP) to the phone and asking the user to return it to verify the subscription request. The process looks like this:
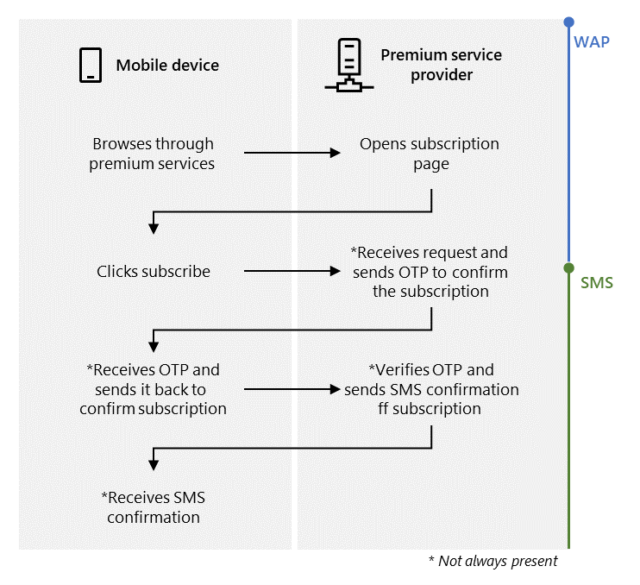
Microsoft
The purpose of the malicious apps is to automatically subscribe infected phones to these WAP services, without the owner’s notification or consent. Microsoft said malicious Android apps that the researchers analyzed achieve this goal by following these steps:
- Turn off the Wi-Fi connection or wait for the user to switch to a mobile network
- Silently navigate to the subscription page
- Automatically click the subscription button
- Intercept the OTP (if applicable)
- Send the OTP to the service provider (if applicable)
- Cancel the SMS notifications (if applicable)
Malware developers have several ways to force a phone to use a cellular connection even when it is connected to Wi-Fi. On devices with Android 9 or earlier, the developers can de setWifiEnabled method of the WifiManager class. For versions 10 and above, developers can use the requestNetwork function of the ConnectivityManager class. Eventually, phones will load data exclusively over the cellular network, as shown in this image:
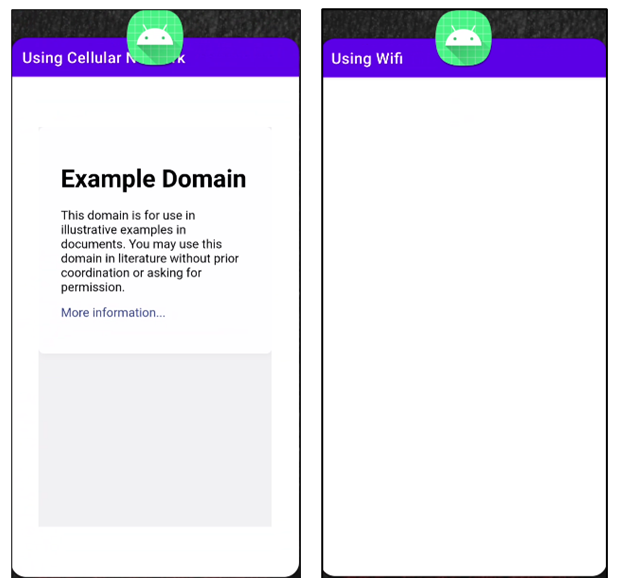
Microsoft
Once a phone uses the mobile network for data transfer, the malicious app stealthily opens a browser in the background, navigates to the WAP subscription page and clicks a subscribe button. Confirming the subscription can be tricky, as confirmation prompts can come via SMS, HTTP, or USSD protocols. Microsoft explains specific methods that malware developers can use to bypass each type of confirmation. The Microsoft post then explains how the malware suppresses periodic messages that the subscription service can send the user to remind them of their subscription.
“By subscribing users to premium services, this malware could lead to victims receiving significant mobile billing fees,” Microsoft researchers wrote. variant will be removed.”
Google actively blocks apps from its Play market when it detects signs of fraud or maliciousness, or when it receives notifications of malicious apps from third parties. While Google often doesn’t remove malicious apps until they infect millions of users, apps downloaded from Play are generally considered more trustworthy than apps from third-party markets.

