
Getty Images
On March 1, Russian forces invading Ukraine knocked out a TV tower in Kiev after the Kremlin announced its intention to destroy “disinformation” in the neighboring country. That public act of kinetic destruction was accompanied by a much more covert but no less damaging action: targeting a prominent Ukrainian broadcaster with malware to render its computers useless.
The double action is one of many examples of the “hybrid war” Russia has waged against Ukraine since the invasion began, according to a report released Wednesday from Microsoft. Shortly before the invasion, the company said, hackers in six groups affiliated with the Kremlin launched no fewer than 237 operations in conjunction with the physical attacks on the battlefield. Nearly 40 of them, targeting hundreds of systems, used wiper malware, which deletes critical files stored on hard drives so the machines can’t boot.
“As today’s report indicates, Russia’s use of cyber-attacks appears to be highly correlated with, and sometimes directly timed, with its kinetic military operations targeting services and institutions critical to civilians,” wrote Tom Burt, Microsoft’s corporate vice president for customer security. He said the “ruthless and destructive Russian cyberattacks” were of particular concern because many of them targeted critical infrastructure that could have cascading negative effects on the country.
It is not clear whether the Kremlin is coordinating cyber operations with kinetic attacks or whether they are the result of independent agencies pursuing a common goal of disrupting or degrading the Ukrainian military and government, while increasing citizens’ trust in those institutions. undermined. What is undeniable is that the two components in this hybrid war have complemented each other.
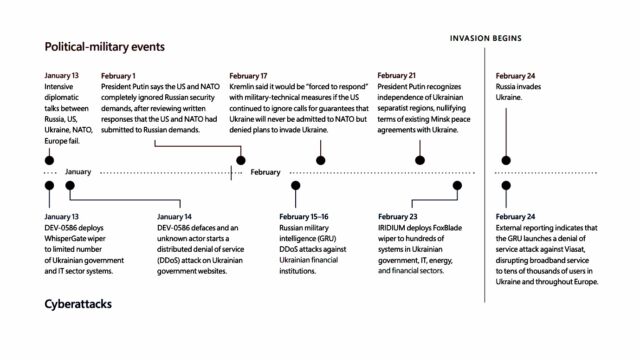
Examples of Russian cyber actions related to political or diplomatic development against Ukraine before the invasion began include:
- The deployment of wiper malware called WhisperGate on a “limited number” of Ukrainian government and IT sector networks on January 3 and the defacement and DDoSing of Ukrainian websites a day later. Those actions came as diplomatic talks between Russia and Ukrainian allies failed.
- DDoS attacks on Ukrainian financial institutions on February 15 and 16. On February 17, the Kremlin said it would be “forced” to respond with military-technical measures if the US did not capitulate to the Kremlin’s demands.
- The February 23 deployment of wiper malware by another Russian state group on hundreds of Ukrainian systems in the government, IT, energy and financial sectors. Two days earlier, Putin recognized the independence of Ukrainian separatists who sided with Russia.
Microsoft
Russia stepped up its cyber offensive as the investigation began. Highlights include:
-
- The compromises of February 14 and February 17 of critical infrastructure in the Ukrainian cities of Odessa and Sumy. These actions seemed to pave the way for February 24, when Russian tanks entered Sumy.
- On March 2, Russian hackers dug into the network of a Ukrainian nuclear power company. A day later, Russian troops occupied Ukraine’s largest nuclear power plant.
- On March 11, a government agency in Dnipro was attacked with a destructive implant. On the same day, Russian troops launched attacks on government buildings in Dnipro.
Wednesday’s report said that as early as March 2021, hackers allied with Russia were preparing for conflict with its neighbor by escalating actions against organizations within or aligned with Ukraine.
The actions have not stopped since then. Burt wrote:
When Russian troops first started moving towards the border with Ukraine, we saw attempts to gain the first access to targets that could provide information about Ukraine’s military and foreign partnerships. In mid-2021, Russian actors targeted supply chain suppliers in Ukraine and abroad to gain further access not only to systems in Ukraine, but also to NATO member states. In early 2022, as diplomatic efforts failed to de-escalate mounting tensions over Russia’s military buildup along Ukraine’s borders, Russian actors launched destructive wiper malware attacks on Ukrainian organizations with increasing intensity. Since the Russian invasion of Ukraine began, Russian cyber-attacks have been deployed to support the military’s strategic and tactical objectives. It is likely that the attacks we have observed are only a fraction of the activities targeting Ukraine.
The report lists a variety of security measures that potential targets of Russian cyber-attacks can take to protect themselves. One measure includes enabling a feature called Watched Folders. The feature, which is not enabled by default, is designed to protect data in specific folders from being destroyed by ransomware, erasers, and other types of destructive malware.

