
MOVEit, the file transfer software exploited in recent weeks in one of the largest cyberattacks ever, has received another security update that fixes a critical vulnerability that can be exploited by malicious people to gain access to large amounts of sensitive data.
On Thursday, MOVEit maker Progress Software published a security bulletin containing fixes for three newly discovered vulnerabilities in the file transfer application. The most serious, tracked as CVE-2023-36934, allows an unauthenticated attacker to gain unauthorized access to the application database. It stems from a security flaw that enables SQL injection, one of the oldest and most common exploit classes.
The vulnerability contains the same elements — and likely the same potentially devastating consequences — as a vulnerability that came to light in late May when members of the Clop ransomware crime syndicate massively exploited it on vulnerable networks around the world. To date, the Clop offensive has affected 229 organizations and distributed data affecting more than 17 million people, according to statistics tracked by Brett Callow, an analyst at security firm Emsisoft. Victims include DMVs in Louisiana and Oregon, the New York City Department of Education, and energy companies Schneider Electric and Siemens Electric.
There are no known reports of the new vulnerability being under active exploitation, but given its severity and past experience, Progress Software and security professionals are urging all MOVEit users to install it immediately. In addition to CVE-2023-36934, Thursday’s security update fixes two additional vulnerabilities. All of them have been discovered by security companies HackerOne and Trend Micro.
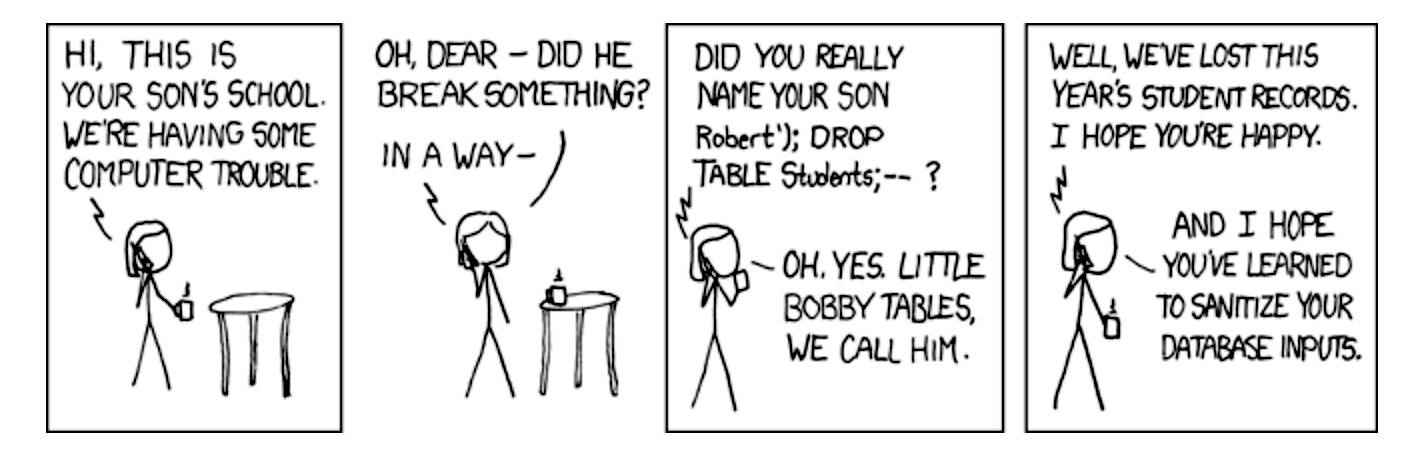
Developers, meet Bobby Tables
One thing that makes CVE-2023-36934 and the earlier vulnerability exploited by Clop so critical is that they can be exploited by people who are not even logged into the system they are hacking into. Both also stem from bugs that enable SQL Injection, a vulnerability class with a long history of exploitation. Often abbreviated as SQLi, it stems from a web application’s failure to correctly query backend databases. SQL syntax uses apostrophes to indicate the beginning and end of a data series. The apostrophes allow SQL parsers to distinguish between data strings and database commands.
Improperly written web apps can sometimes interpret data entered as commands. Hackers can exploit these flaws by entering strings containing apostrophes or other special characters into web fields that cause backend databases to do things the developers never intended to do. Attacks like this have formed the basis for some of the greatest compromises in history. In addition to the recent Clop attack, there are two other notable examples: the Heartland Payment Systems hack in 2007, which allowed convicted hacker Albert Gonzalez to steal data for 130 million credit cards, and the HBGary compromise in 2011.
SQL injection is the subject of an xkcd cartoon featuring Bobby Tables, a student whose full name is ‘Robert’); WASTE TABLE Students;–?” (without the quotation marks). When the school computer system tries to process its name, it only interprets “Robert” as data and processes “DROP TABLE” as the dangerous SQL command to delete data. As a result, the school loses an entire year’s records.
A second vulnerability fixed in Thursday’s MOVEit security update is also the result of SQLi bugs. Progress Software said it “could allow an authenticated attacker to gain unauthorized access to the MOVEit Transfer database. An attacker could submit a crafted payload to a MOVEit Transfer application endpoint, which could result in modification and disclosure of MOVEit database contents.
The third vulnerability that has been fixed, CVE-2023-36933, allows hackers to unexpectedly terminate the MOVEit application. The last two vulnerabilities have a severity that is described as high.
The vulnerabilities affect multiple MOVEit Transfer versions, from 12.0.x to 15.0.x. Given the damage that resulted from Clop’s massive exploitation of the previous MOVEit vulnerability, the latest patches should be installed as soon as possible. Sorry, admins, but if that means working late on a Friday or weekend, that’s a better option than waking up to a world of pain on Monday morning.

