
Secure Boot is an industry standard that ensures that Windows devices do not load malicious firmware or software during the boot process. If you’ve enabled it – as you should in most cases, and it’s the default setting imposed by Microsoft – good for you. However, if you’re using one of the more than 300 motherboard models made by manufacturer MSI in the last 18 months, you may not be protected.
Introduced in 2011, Secure Boot establishes a chain of trust between the hardware and software or firmware that boots a device. Before Secure Boot, devices used software known as the BIOS, installed on a small chip, to instruct them how to boot and recognize and start hard drives, CPUs, memory, and other hardware. Once completed, this mechanism loaded the bootloader, which activates tasks and processes for loading Windows.
The problem was, the BIOS loaded every bootloader that was in the correct folder. That permissiveness allowed hackers with short-term access to a device to install rogue boot loaders that would in turn run malicious firmware or Windows images.
When Secure Boot falls apart
About a decade ago, the BIOS was replaced by the UEFI (Unified Extensible Firmware Interface), a standalone operating system that could prevent the loading of system drivers or bootloaders that were not digitally signed by their trusted manufacturers.
UEFI relies on both trusted and revoked signature databases that OEMs load into motherboard non-volatile memory during manufacture. The signatures list the signers and cryptographic hashes of each authorized bootloader or UEFI-driven application, a measure that establishes the chain of trust. This chain ensures that the device boots securely using only code that is known and trusted. If unknown code needs to be loaded, Secure Boot terminates the boot process.
A researcher and student recently discovered that more than 300 motherboard models from Taiwan-based MSI do not implement Secure Boot by default and run any bootloader. The models work with a variety of hardware and firmware, including many from Intel and AMD (the full list is here). The shortcoming was introduced sometime in the third quarter of 2021. The researcher accidentally discovered the problem while attempting to digitally sign various parts of his system.
“On 12/11/2022 I decided to set up Secure Boot on my new desktop using sbctl,” wrote Dawid Potocki, a Polish-born researcher now living in New Zealand. “Unfortunately, I found that my firmware… accepted any OS image I gave it, whether it was trusted or not. It wasn’t the first time I signed Secure Boot myself, I didn’t do it wrong.”
Potocki said he found no indication that motherboards from manufacturers ASRock, Asus, Biostar, EVGA, Gigabyte and NZXT have the same shortcoming.
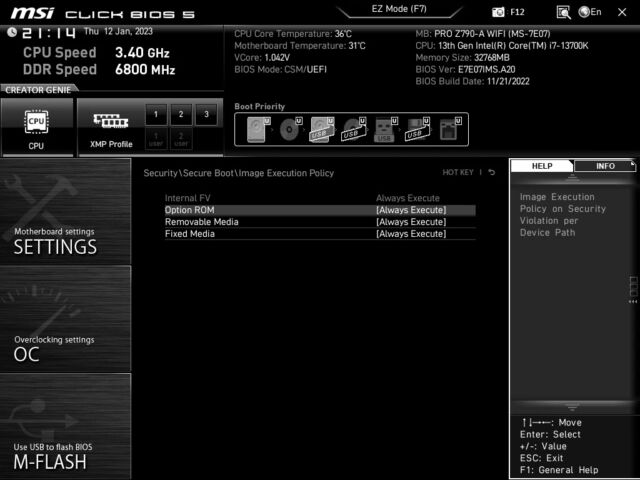
The researcher further reported that the broken Secure Boot was the result of MSI inexplicably changing the default settings. Users who want to implement Secure Boot – which really should be everyone – need to access the settings on their affected motherboard. To do this, hold down the Del button on the keyboard while the device boots up. From there, select the menu that says Security\Secure Boot or something similar and then select the Image Execution Policy sub menu. If your motherboard is compromised, Removable Media and Fixed Media will be set to “Always Run”.
Getty Images
To fix this, change “Always execute” for these two categories to “Deny execute”.
In a Reddit post published Thursday, an MSI representative confirmed Potocki’s findings. The rep wrote:
We’ve set Secure Boot Preemptive as Enabled and “Always Run” as the default setting to provide a user-friendly environment that gives multiple end users the flexibility to build their PC systems with thousands (or more) of components that include their built-in option ROM, including OS images, resulting in higher compatibility configurations. For users who are very concerned about security, they can still set “Image Execution Policy” as “Deny Execution” or set other options manually to meet their security needs.
The post said that MSI will release new firmware versions that will change the defaults to “Deny Execute”. The subreddit linked above contains a discussion that can help users troubleshoot.
As mentioned earlier, Secure Boot is designed to prevent attacks where an untrusted person stealthily gains brief access to a device and tampers with its firmware and software. Such hacks are usually known as “Evil Maid attacks”, but a better description is “Stalker Ex-Boyfriend attacks”.

